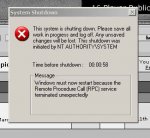
...and that"s what it does:
"
When W32.Blaster.Worm is executed, it does the following:
1. Creates a Mutex named "BILLY." If the mutex exists, the worm will exit.
2. Adds the value:
"windows auto update"="msblast.exe"
to the registry key:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
so that the worm runs when you start Windows.
3. Calculates the IP address, based on the following algorithm, 40% of the time:
Host IP: A.B.C.D
sets D equal to 0.
if C > 20, will subtract a random value less than 20.
Once calculated, the worm will start attempting to exploit the computer based on A.B.C.0, and then count up.
NOTE: This means the Local Subnet will become saturated with port 135 requests prior to exiting the local subnet.
4. Calculates the IP address, based on many random numbers, 60% of the time:
A.B.C.D
set D equal to 0.
sets A, B, and C to random values between 0 and 255.
5. Sends data on TCP port 135 that may exploit the DCOM RPC vulnerability to allow the following actions to occur on the vulnerable computer:
Create a hidden Cmd.exe remote shell that will listen on TCP port 4444.
NOTE: Due to the random nature of how the worm constructs the exploit data, it may cause computers to crash if it sends incorrect data.
6. Listens on UDP port 69. When the worm receives a request, it will return the Msblast.exe binary.
7. Sends the commands to the remote computer to reconnect to the infected host and to download and run Msblast.exe.
8. If the current month is after August, or if the current date is after the 15th, the worm will perform a DoS on "windowsupdate.com."
With the current logic, the worm will activate the DoS attack on the 16th of this month, and continue until the end of the year.
The worm contains the following text, which is never displayed:
I just want to say LOVE YOU SAN!!
billy gates why do you make this possible ? Stop making money and fix your software!!......"
Great sense of houmor from these guys...